(70007)the Timeout Specified Has Expired Ssl Input Filter Read Failed
In concluding blog, I introduced how SSL/TLS connections are established and how to verify the whole handshake procedure in network packet file. Yet capturing network parcel is not ever supported or possible for certain scenarios. Hither in this blog, I will innovate 5 handy tools that can test dissimilar phases of SSL/TLS connexion so that you lot can narrow down the crusade of SSL/TLS connexion effect and locate root crusade.
curlicue
Suitable scenarios: TLS version mismatch, no supported CipherSuite, network connexion between client and server.
curl is an open source tool bachelor on Windows 10, Linux and Unix OS. It is a tool designed to transfer data and supports many protocols. HTTPS is one of them. Information technology can also used to test TLS connection.
Examples:
1. Test connexion with a given TLS version.
curl -v https://pingrds.redis.enshroud.windows.net:6380 --tlsv1.0
two. Test with a given CipherSuite and TLS version
scroll -v https://pingrds.redis.cache.windows.net:6380 --ciphers ECDHE-RSA-NULL-SHA --tlsv1.2
Success connection example:
scroll -v https://pingrds.redis.cache.windows.net:6380 --tlsv1.2 * Rebuilt URL to: https://pingrds.redis.enshroud.windows.net:6380/ * Trying 13.75.94.86... * TCP_NODELAY set * Connected to pingrds.redis.cache.windows.net (13.75.94.86) port 6380 (#0) * schannel: SSL/TLS connection with pingrds.redis.cache.windows.cyberspace port 6380 (pace 1/3) * schannel: checking server document revocation * schannel: sending initial handshake data: sending 202 bytes... * schannel: sent initial handshake data: sent 202 bytes * schannel: SSL/TLS connexion with pingrds.redis.cache.windows.internet port 6380 (pace ii/3) * schannel: failed to receive handshake, demand more data * schannel: SSL/TLS connexion with pingrds.redis.cache.windows.cyberspace port 6380 (footstep two/three) * schannel: encrypted information got 4096 * schannel: encrypted information buffer: kickoff 4096 length 4096 * schannel: received incomplete message, need more data * schannel: SSL/TLS connection with pingrds.redis.enshroud.windows.internet port 6380 (stride 2/3) * schannel: encrypted data got 1024 * schannel: encrypted data buffer: offset 5120 length 5120 * schannel: received incomplete message, need more information * schannel: SSL/TLS connexion with pingrds.redis.cache.windows.net port 6380 (step two/3) * schannel: encrypted data got 496 * schannel: encrypted data buffer: starting time 5616 length 6144 * schannel: sending adjacent handshake data: sending 3791 bytes... * schannel: SSL/TLS connection with pingrds.redis.enshroud.windows.net port 6380 (pace 2/3) * schannel: encrypted data got 51 * schannel: encrypted information buffer: offset 51 length 6144 * schannel: SSL/TLS handshake consummate * schannel: SSL/TLS connection with pingrds.redis.cache.windows.net port 6380 (step iii/three) * schannel: stored credential handle in session cache Fail connection case due to either TLS version mismatch. Not supported ciphersuite returns similar error.
curl -v https://pingrds.redis.cache.windows.internet:6380 --tlsv1.0 * Rebuilt URL to: https://pingrds.redis.enshroud.windows.cyberspace:6380/ * Trying 13.75.94.86... * TCP_NODELAY set up * Connected to pingrds.redis.enshroud.windows.net (xiii.75.94.86) port 6380 (#0) * schannel: SSL/TLS connection with pingrds.redis.cache.windows.cyberspace port 6380 (step 1/3) * schannel: checking server certificate revocation * schannel: sending initial handshake information: sending 144 bytes... * schannel: sent initial handshake data: sent 144 bytes * schannel: SSL/TLS connection with pingrds.redis.enshroud.windows.net port 6380 (step two/3) * schannel: failed to receive handshake, need more data * schannel: SSL/TLS connection with pingrds.redis.cache.windows.net port 6380 (footstep 2/three) * schannel: failed to receive handshake, SSL/TLS connexion failed * Closing connection 0 * schannel: shutting down SSL/TLS connection with pingrds.redis.cache.windows.net port 6380 * Send failure: Connection was reset * schannel: failed to send close msg: Failed sending data to the peer (bytes written: -one) * schannel: clear security context handle curl: (35) schannel: failed to receive handshake, SSL/TLS connection failed Failed due to network connectivity event.
curlicue -five https://pingrds.redis.cache.windows.net:6380 --tlsv1.2 * Rebuilt URL to: https://pingrds.redis.enshroud.windows.net:6380/ * Trying 13.75.94.86... * TCP_NODELAY ready * connect to 13.75.94.86 port 6380 failed: Timed out * Failed to connect to pingrds.redis.cache.windows.cyberspace port 6380: Timed out * Closing connexion 0 roll: (7) Failed to connect to pingrds.redis.enshroud.windows.net port 6380: Timed out openssl
Suitable scenarios: TLS version mismatch, no supported CipherSuite, network connection betwixt client and server.
openSSL is an open source tool and its s_client acts as SSL client to test SSL connection with a remote server. This is helpful to isolate the cause of client.
- On majority Linux machines, OpenSSL is there already. On Windows, you tin download it from this link: https://chocolatey.org/packages/openssl
- Run Open SSL
- Windows: open the installation directory, click /bin/, and then double-click openssl.exe.
- Mac and Linux: run openssl from a terminal.
- Consequence s_client -help to find all options.
Control examples:
i. Test a item TLS version:
s_client -host sdcstest.hulk.cadre.windows.internet -port 443 -tls1_1
ii. Disable ane TLS version
s_client -host sdcstest.blob.core.windows.net -port 443 -no_tls1_2
3. Test with a given ciphersuite:
s_client -host sdcstest.hulk.core.windows.net -port 443 -nix ECDHE-RSA-AES256-GCM-SHA384
4. Verify if remote server's certificates are trusted.
Success connexion example:
Continued(000001A0) depth=i C = US, O = Microsoft Corporation, CN = Microsoft RSA TLS CA 02 verify mistake:num=20:unable to get local issuer certificate verify render:ane depth=0 CN = *.blob.cadre.windows.net verify return:1 --- Certificate chain 0 south:CN = *.blob.core.windows.internet i:C = United states of america, O = Microsoft Corporation, CN = Microsoft RSA TLS CA 02 ane s:C = The states, O = Microsoft Corporation, CN = Microsoft RSA TLS CA 02 i:C = IE, O = Baltimore, OU = CyberTrust, CN = Baltimore CyberTrust Root --- Server certificate -----Brainstorm CERTIFICATE----- MIINtDCCC5ygAwIBAgITfwAI6NfesKGuQGWPYQAAAAjo1zANBgkqhkiG9w0BAQsF ADBPMQswCQYDVQQGEwJVUzEeMBwGA1UEChMVTWljcm9zb2Z0IENvcnBvcmF0aW9u pK8hqxL0zc4NQLRTq9RNpdPwnNmGn5SZ4Nu5ktUgWokR97THzgs6a/ErHH2tigLF jwkgB8UuV/hhu3vEa0jxstSBgbjQPgSNexAl7XwgawaucIF+wkRpPW2w0VTcDWtT 1bGtFCpewAo= -----Finish Document----- subject field=CN = *.blob.core.windows.net issuer=C = US, O = Microsoft Corporation, CN = Microsoft RSA TLS CA 02 --- No client certificate CA names sent Peer signing digest: MD5-SHA1 Peer signature type: RSA Server Temp Central: ECDH, P-256, 256 $.25 --- SSL handshake has read 5399 bytes and written 293 bytes Verification fault: unable to get local issuer certificate --- New, TLSv1.0, Cipher is ECDHE-RSA-AES256-SHA Server public key is 2048 flake Secure Renegotiation IS supported Compression: NONE Expansion: NONE No ALPN negotiated SSL-Session: Protocol : TLSv1.1 Nothing : ECDHE-RSA-AES256-SHA Session-ID: B60B0000F51FFB7C9DDB4E58CD20DC20987C13CFD31386BE435D612CF5EFDBF9 Session-ID-ctx: Main-Cardinal: DA402F6E301B4E4981B7820CAF6E0AF3C633290E85E2998BFAB081788488D3807ABD3FF41FF48DA55DB56281C024C4F4 PSK identity: None PSK identity hint: None SRP username: None Showtime Time: 1615557502 Timeout : 7200 (sec) Verify render lawmaking: 20 (unable to get local issuer certificate) Extended master cloak-and-dagger: yep Fail connection instance due to TLS mismatch:
OpenSSL> s_client -host sdcstest.hulk.core.windows.internet -port 443 -tls1_3 Continued(0000017C) write:errno=10054 --- no peer document available --- No client document CA names sent --- SSL handshake has read 0 bytes and written 254 bytes Verification: OK --- New, (NONE), Cipher is (NONE) Secure Renegotiation IS Not supported Pinch: NONE Expansion: NONE No ALPN negotiated Early on data was not sent Verify return lawmaking: 0 (ok) --- mistake in s_client Neglect connection example due to network connectivity:
OpenSSL> s_client -host sdcstest.hulk.core.windows.net -port 7780 30688:error:0200274C:system library:connect:reason(1868):crypto/bio/b_sock2.c:110: 30688:error:2008A067:BIO routines:BIO_connect:connect error:crypto/bio/b_sock2.c:111: connect:errno=0 mistake in s_client Online tool
https://world wide web.ssllabs.com/ssltest/
Suitable scenarios: TLS version mismatch, no supported CipherSuite.
This is a free online service performs a deep analysis of the configuration of whatever SSL web server on the public Cyberspace. It can list all supported TLS versions and ciphers of a server. And machine detect if server works fine in unlike types of client, such as web browsers, mobile devices, etc.
Delight note, this just works with public access website. For internal access website will need to run above curl or openssl from an internal surround. And it only supports domain name and does not work with IP address.
Web Browser:
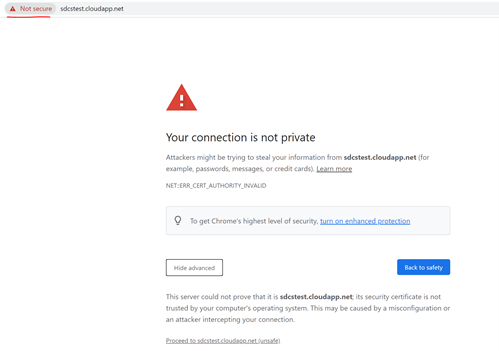
Suitable scenarios: Verify if server certificate chain is trusted on client.
Web Browser tin can exist used to verify if remote server's certificate is trusted or non locally:
- Admission the url from web browser.
- It does not thing if the folio can be load or not. Before loading anything from the remote sever, web browser tried to constitute SSL connexion.
- If you lot encounter below error returned, information technology means document is not trusted on current machine.
Certutil
Suitable scenarios: Verify if server certificate on client, verify client certificate on server.
Certutil is a tool available on windows. Information technology is useful to verify a given certificate. For case verify server certificate from client end. If mutual authentication is implemented, this tool can likewise be used to verify client certificate on server.
The command car verifies trusted certificate chain and document revocation list (CRL).
Command:
certutil -verify -urlfetch <customer cert file path>
https://docs.microsoft.com/en-u.s./windows-server/administration/windows-commands/certutil#-verify
Next weblog, I will introduce solutions for common causes of SSL/TLS connection problems.
Source: https://techcommunity.microsoft.com/t5/azure-paas-blog/ssl-tls-connection-issue-troubleshooting-test-tools/ba-p/2240059
0 Response to "(70007)the Timeout Specified Has Expired Ssl Input Filter Read Failed"
Enregistrer un commentaire